Introduction:
In today’s digital landscape, cybersecurity is a top priority for businesses of all sizes. With cyber threats becoming increasingly sophisticated, traditional security measures are no longer sufficient to protect sensitive data and assets. Enter the Zero Trust security model – a revolutionary approach that challenges the conventional wisdom of perimeter-based security. As leading experts in software security, QWERTY EXPERTS is here to explore the principles of Zero Trust and how it represents a paradigm shift in safeguarding your digital infrastructure.
Understanding the Zero Trust Security Model:
What is Zero Trust?

Zero Trust is a security framework based on the principle of “never trust, always verify.” Unlike traditional security models that rely on perimeter defenses, Zero Trust assumes that threats may already exist within the network and requires continuous verification of trust for every user, device, and application attempting to access resources.
Key Components of Zero Trust:
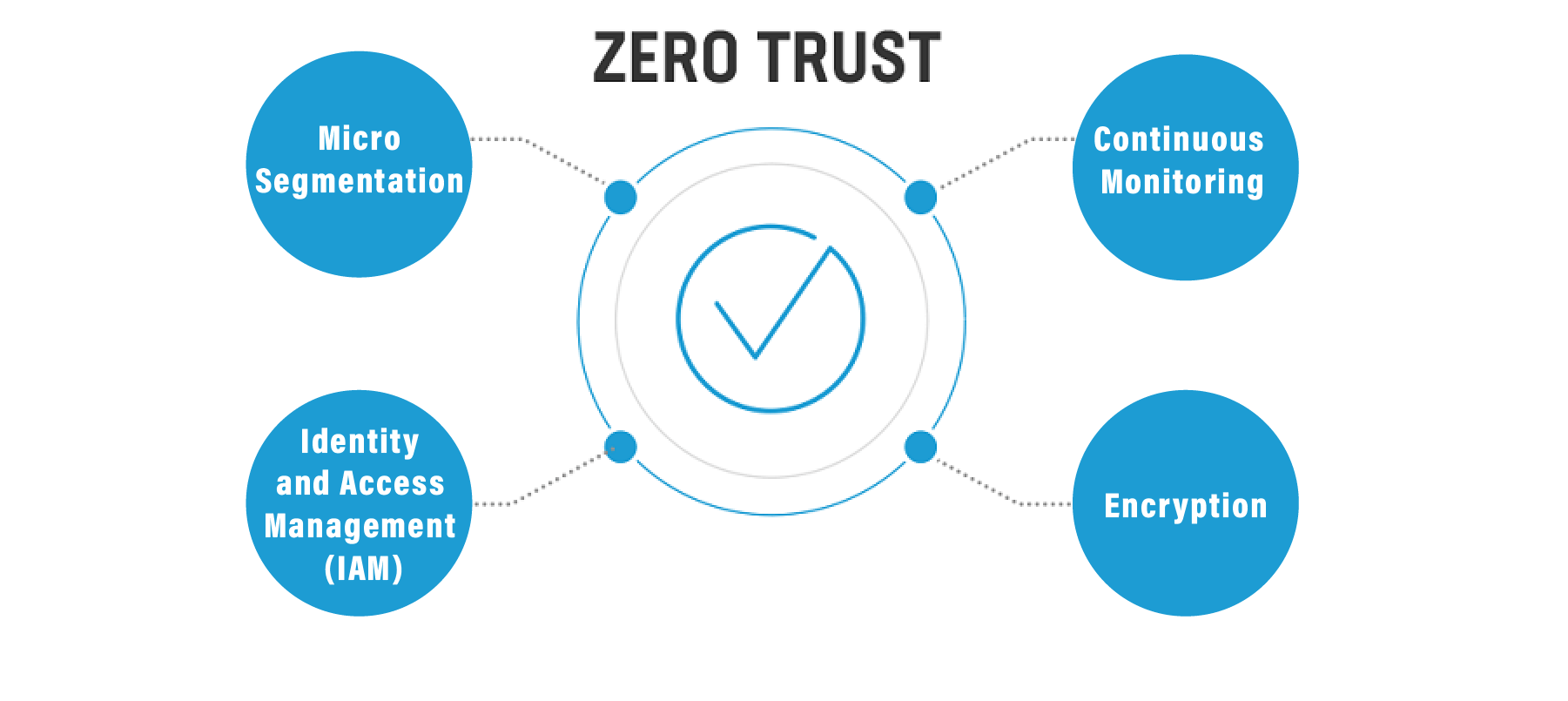
Micro-Segmentation:
Segmenting the network into smaller, isolated zones to minimize the lateral movement of threats and restrict access based on user identity, device health, and other contextual factors.
Identity and Access Management (IAM):
Implementing strong authentication mechanisms, least privilege access controls, and multi-factor authentication to verify user identities and enforce granular access policies.
Continuous Monitoring:
Employing real-time monitoring, analytics, and threat intelligence to detect anomalous behavior and potential security incidents, enabling proactive response and remediation.
Encryption:
Encrypting data both in transit and at rest to protect sensitive information from unauthorized access, ensuring confidentiality and integrity across the network.
The Advantages of Zero Trust Security:
Enhanced Security Posture:
By eliminating the assumption of trust and adopting a “verify-first” approach, Zero Trust minimizes the attack surface and mitigates the risk of unauthorized access, data breaches, and insider threats.
Improved Compliance:
Zero Trust aligns with regulatory requirements and industry best practices, providing businesses with a robust framework for achieving and maintaining compliance with data protection standards such as GDPR, HIPAA, and PCI DSS.
Flexibility and Scalability:
The modular nature of Zero Trust allows organizations to adapt security controls based on evolving threats, business needs, and technological advancements, ensuring scalability and future-proofing their security posture.
Enhanced User Experience:
Despite its stringent security measures, Zero Trust is designed to facilitate seamless access to resources for authorized users, reducing friction and enhancing productivity without compromising security.
How QWERTY EXPERTS Can Help:
At QWERTY EXPERTS, we understand the critical importance of robust security measures in today’s interconnected world. Our team of cybersecurity professionals specializes in implementing Zero Trust security solutions tailored to your organization’s unique requirements.
Our Zero Trust Security Services Include:

Assessment and Strategy:
We conduct comprehensive security assessments to identify vulnerabilities and design a tailored Zero Trust strategy aligned with your business objectives.
Implementation and Integration:
Our experts deploy and integrate Zero Trust technologies seamlessly into your existing infrastructure, ensuring minimal disruption and maximum efficacy.
Monitoring and Management:
We provide continuous monitoring, threat detection, and incident response services to proactively safeguard your digital assets and respond swiftly to emerging threats.
Training and Education:
We offer training programs and workshops to empower your staff with the knowledge and skills needed to uphold Zero Trust principles and practices effectively.
Conclusion:
In conclusion, the Zero Trust security model represents a fundamental shift in how organizations approach cybersecurity – from trust-based to trust-agnostic. By adopting a Zero Trust mindset and leveraging advanced technologies and strategies, businesses can strengthen their security posture, mitigate risks, and safeguard their most valuable assets in an increasingly hostile digital environment. Partner with QWERTY EXPERTS to embark on your Zero Trust journey and ensure a secure and resilient future for your organization.
Let’s embrace the paradigm shift together – where trust is earned, not assumed, and where security is not just a goal but a fundamental principle of digital resilience.
Closing Thoughts:
In conclusion, the Zero Trust security model represents a paradigm shift in software security, challenging traditional notions of trust and redefining how organizations protect their critical assets. As cyber threats continue to evolve in sophistication and scale, adopting a Zero Trust approach is no longer a choice but a necessity for safeguarding sensitive data and systems.
At QWERTY EXPERTS, we are committed to empowering organizations with robust and resilient security solutions that mitigate risk and enable business innovation. By embracing the principles of Zero Trust, organizations can enhance their security posture, achieve regulatory compliance, and build a foundation for long-term resilience in the face of evolving cyber threats.
Let QWERTY EXPERTS be your trusted partner in navigating the complexities of software security. Together, we can embrace the zero-trust paradigm and usher in a new era of confidence, resilience, and trust in the digital landscape. Contact us today to embark on your journey towards a more secure future.